The Petya / Petrwrap ransomware has been actively spreading over the last few days. It is the first major attack when we can use a new surveillance center with integrated data acquisition from the Turris routers, so let's take a look at several outputs.
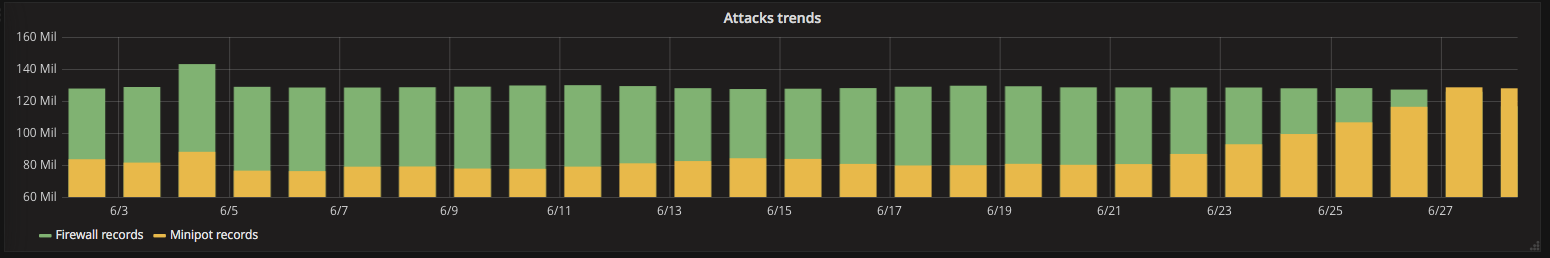
Since June 22, the number of infected computers has dramatically increased, as we see in the rapid growth of honeypot records. Honeypot records indicate the number of attempted unauthorized login to "naively secure client devices" emulated by our servers. The previously quite stable level has so far been disturbed by isolated attacks, but after 22.6. The number of honeypot records increases by half and grows only moderately.
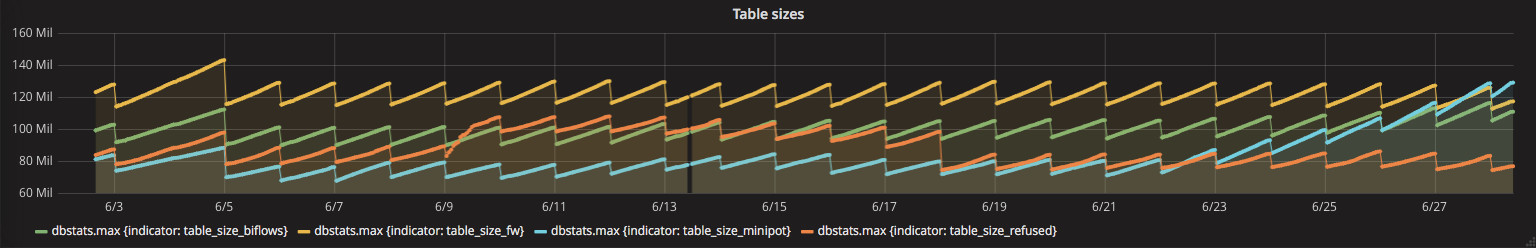
It is also interesting to note that in the first third of June, the number of refused connections has increased significantly, indicating the number of attempts to connect to the Internet in which the counterparty did not respond. Such records are now typical of malware and ransomware that connect to the Internet on already inactive control servers or attempt to spread the Internet.
From the data, we might conclude that we are moving near the peak of the Petya attack and its largest current wave (until further modification) is dropped. But that does not mean that unsecured computers can not be attacked. The Turris routers do not actively filter the contents and can not prevent infected computer ransomware spreading through e-mail or otherwise to the local network. Learn more about Petya's protection at csirt.cz website.
You can also help increase everyone's security - enable data collection for these security analytics on your Turris Omnia router.